Version 2.0 – July 2022
In September 2022, the Department of Defense (DoD) released version 2.0 of its Zero Trust Reference Architecture (ZTRA). The document outlines a set of principles and best practices for implementing a Zero Trust security model. In this blog post, we’ll take a closer look at what Zero Trust is, the key concepts outlined in the ZTRA document, the seven pillars of Zero Trust, what to take away from the document, criticisms of Zero Trust, and our conclusion.

What is Zero Trust?
Zero Trust is a security model that assumes that all users, devices, and applications are untrusted by default, regardless of their location. It operates on the principle of “never trust, always verify.” The goal of Zero Trust is to minimize the risk of data breaches by continuously verifying and validating access requests.
Five Key Concepts from ZTRA
The ZTRA v2.0 document identifies five key concepts that are essential to the Zero Trust security model:
- Assume a Hostile Environment: Organizations should assume that the network environment is hostile and that threats are constantly present.
- Presume Breach: Organizations should presume that they have already been breached and that attackers are present in their network.
- Never Trust, Always Verify: Organizations should verify and authenticate all users, devices, and applications before granting access to resources.
- Scrutinize Explicitly: Organizations should explicitly define and control access to resources based on the principle of least privilege.
- Apply Unified Analytics: Organizations should use analytics and automation to monitor and respond to security events across the network.

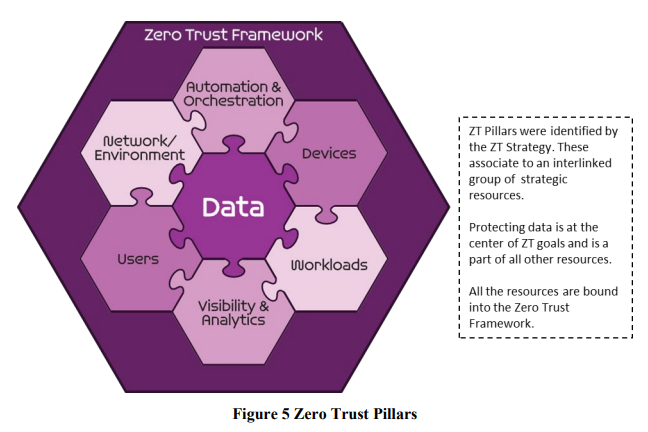
Seven Foundational Pillars
In addition to the five concepts, the ZTRA v2.0 document identifies seven key pillars that form the foundation of a successful Zero Trust implementation. These pillars provide a framework for designing and implementing Zero Trust across an organization’s systems and processes.
The seven pillars are:
- User: The first pillar of Zero Trust is to establish the identity of users and their level of access to resources. This requires strong authentication and authorization mechanisms, including multi-factor authentication, and fine-grained access control.
- Device: Devices used to access an organization’s resources must also be verified and authenticated before being granted access. This includes implementing policies for endpoint security, such as requiring antivirus software, and establishing a device trust score.
- Network/Environment: Traditional network perimeters are no longer sufficient for securing an organization’s resources. Zero Trust requires a focus on securing the network and environment in which systems and data reside. This includes implementing micro-segmentation, network access control, and perimeter security controls.
- Applications and Workload: In a Zero Trust environment, access to applications and workloads is granted based on a user’s identity and level of trust, rather than their location. This requires strong application-level security controls, such as application firewalls and access control lists.
- Data: Protecting data is a critical component of Zero Trust. This includes understanding the sensitivity of data and implementing encryption, data loss prevention, and data classification policies.
- Visibility and Analytics: Visibility into an organization’s systems and data is crucial for detecting and responding to threats. Zero Trust requires implementing advanced analytics and monitoring capabilities, including behavior-based anomaly detection and threat intelligence feeds.
- Automation and Orchestration: Finally, automation and orchestration are essential components of a Zero Trust implementation. This includes automating the deployment of security controls, enforcing security policies, and integrating security processes and tools.
By focusing on these seven pillars, organizations can build a strong Zero Trust foundation that is resilient to cyber threats and helps to protect sensitive data and systems.
Now that we have discussed the five concepts and seven pillars of Zero Trust, let’s take a look at the key takeaways from this document.
Criticisms of Zero Trust
While the Zero Trust security model has gained popularity in recent years, it is not without its criticisms. Some experts argue that Zero Trust is difficult to implement and can lead to increased complexity and costs. Others argue that it may not be suitable for all organizations or use cases.
Key Takeaways
- Zero Trust is an ongoing process, not a one-time solution: Implementing Zero Trust requires ongoing effort, as threats and technology are constantly evolving. It’s important to continually assess and adapt Zero Trust practices to ensure they remain effective.
- Zero Trust requires collaboration across departments and teams: Implementing Zero Trust often involves changes to an organization’s security culture, technology infrastructure, and business processes. Collaboration between IT, security, and business teams is critical to ensure a successful implementation.
- Zero Trust is not a silver bullet: While Zero Trust can significantly improve an organization’s security posture, it is not a complete solution. Other security measures such as strong password policies, network segmentation, and regular vulnerability assessments should still be employed in conjunction with Zero Trust to ensure a comprehensive security strategy.
Conclusion
In conclusion, the Zero Trust approach has emerged as a powerful security framework that helps organizations protect against modern security threats. With the rise of remote work and cloud-based services, implementing Zero Trust is more important than ever before. By assuming a hostile environment, presuming breach, and applying the five core concepts, organizations can create a more secure environment. By following the seven pillars of Zero Trust, organizations can create a holistic and effective security strategy. While Zero Trust is not a silver bullet and requires ongoing effort, collaboration, and constant adaptation, it can significantly improve an organization’s security posture. Overall, Zero Trust represents a powerful and effective approach to modern cybersecurity, and organizations should consider implementing it as part of their overall security strategy.