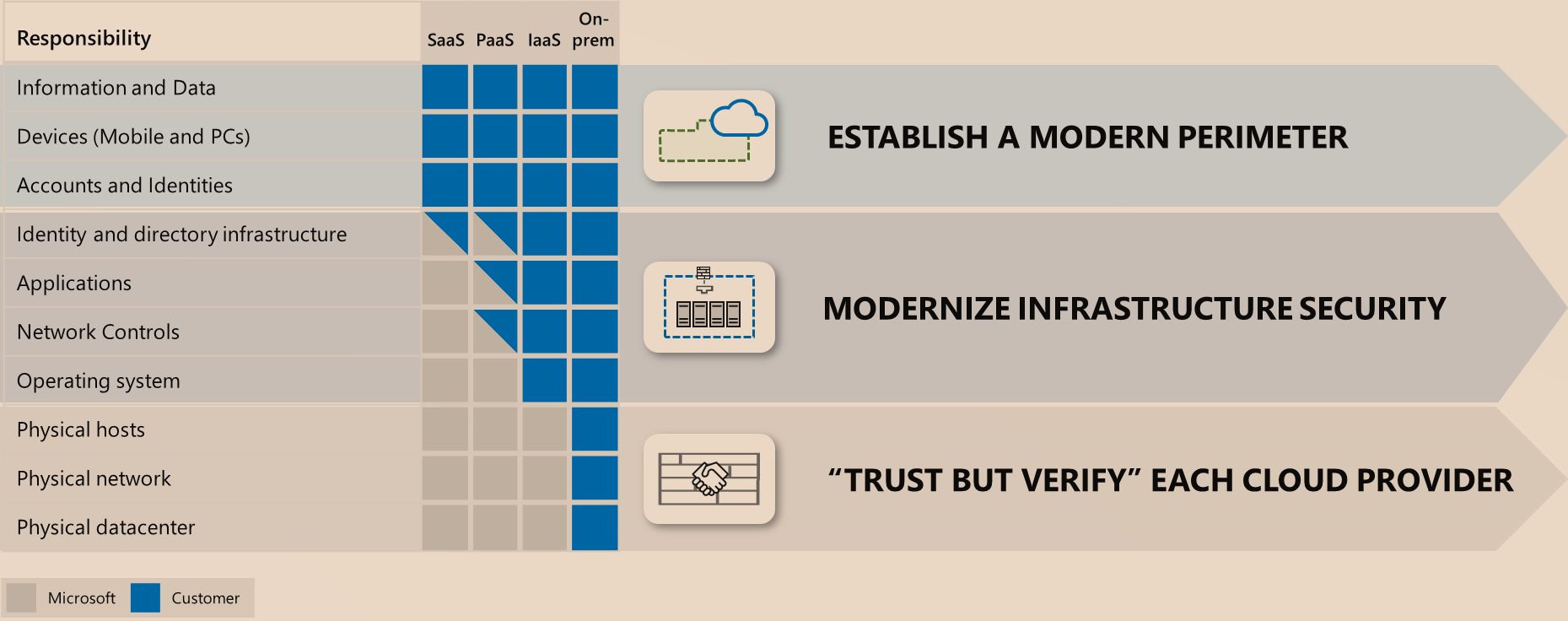
The Azure Well-Architected Framework provides a set of best practices for building and running secure, scalable, and efficient cloud infrastructure on Azure. The framework is divided into five pillars, one of which is Security. This post explores the Security pillar of the Azure Well-Architected Framework and provides an overview of the key concepts.
Why is this a Good Resource?
This overview, like the AWS Security Pillar and AWS Security Reference Architecture, are good general resources to learn about cloud security overall. It includes general practices you need to know and can leverage to build your own cloud strategy if you are multi-cloud or using a different provider other than Azure. There are also Azure best practices that go into further detail on specific domains.
What is the Security Pillar of the Azure Well-Architected Framework?
The Security pillar of the Azure Well-Architected Framework is focused on ensuring that your cloud environment is secure and compliant. It’s designed to provide guidance and best practices for securing your applications and data on Azure.

The Security pillar consists of several key areas:
- Identity and Access Management (IAM): IAM involves managing user identities and their access to resources. This includes implementing strong authentication mechanisms, controlling access permissions, and monitoring activity.
- Threat Protection: Threat protection involves detecting, responding to, and mitigating security threats. This includes implementing security monitoring and incident response procedures, and using threat intelligence to stay up to date on emerging threats.
- Cloud Security: Cloud security involves securing the cloud environment itself, including the underlying infrastructure, platform, and software. This includes implementing security controls to protect against threats such as DDoS attacks and data breaches.
- Information Protection: Information protection involves protecting data at rest and in transit. This includes encrypting sensitive data, implementing backup and recovery procedures, and implementing network security controls.
- Information Governance: Information governance involves managing and protecting data throughout its lifecycle. This includes defining data classification and retention policies, and ensuring compliance with regulatory requirements.
- Insider Risk Management: Insider risk management involves identifying and mitigating risks posed by insiders, such as employees and contractors. This includes implementing access controls and monitoring for suspicious activity.
- Compliance Management: Compliance management involves meeting regulatory requirements and industry standards for security and privacy. This includes implementing security controls and policies to ensure compliance with regulations such as GDPR and HIPAA.
- Discover and Respond: Discover and respond involves detecting, investigating, and responding to security incidents. This includes implementing security monitoring and incident response procedures, and using threat intelligence to identify and mitigate threats.
How Does It Help with Cloud Security?
The Security pillar of the Azure Well-Architected Framework provides a comprehensive approach to cloud security that covers all key areas of security. By following the best practices outlined in the Security pillar, you can help ensure that your cloud environment is secure and compliant. This can help to reduce the risk of security breaches, data loss, and regulatory violations.
Additionally, the Security pillar is designed to be flexible and adaptable to your specific needs. You can use the guidance and best practices to build a secure cloud environment that meets your specific security requirements and objectives.
Conclusion
The Security pillar of the Azure Well-Architected Framework is an essential resource for anyone looking to build a secure and compliant cloud environment on Azure. By following the best practices outlined in the Security pillar, you can help ensure that your cloud environment is secure and protected against threats. We encourage readers to explore the Security pillar of the Azure Well-Architected Framework to learn more about how to build a secure and compliant cloud environment on Azure.